“Advertising Positions: Data Portraiture as Aesthetic Critique” by Howe, Chen and Chen
Conference:
Type(s):
Title:
- Advertising Positions: Data Portraiture as Aesthetic Critique
Presenter(s)/Author(s):
Abstract:
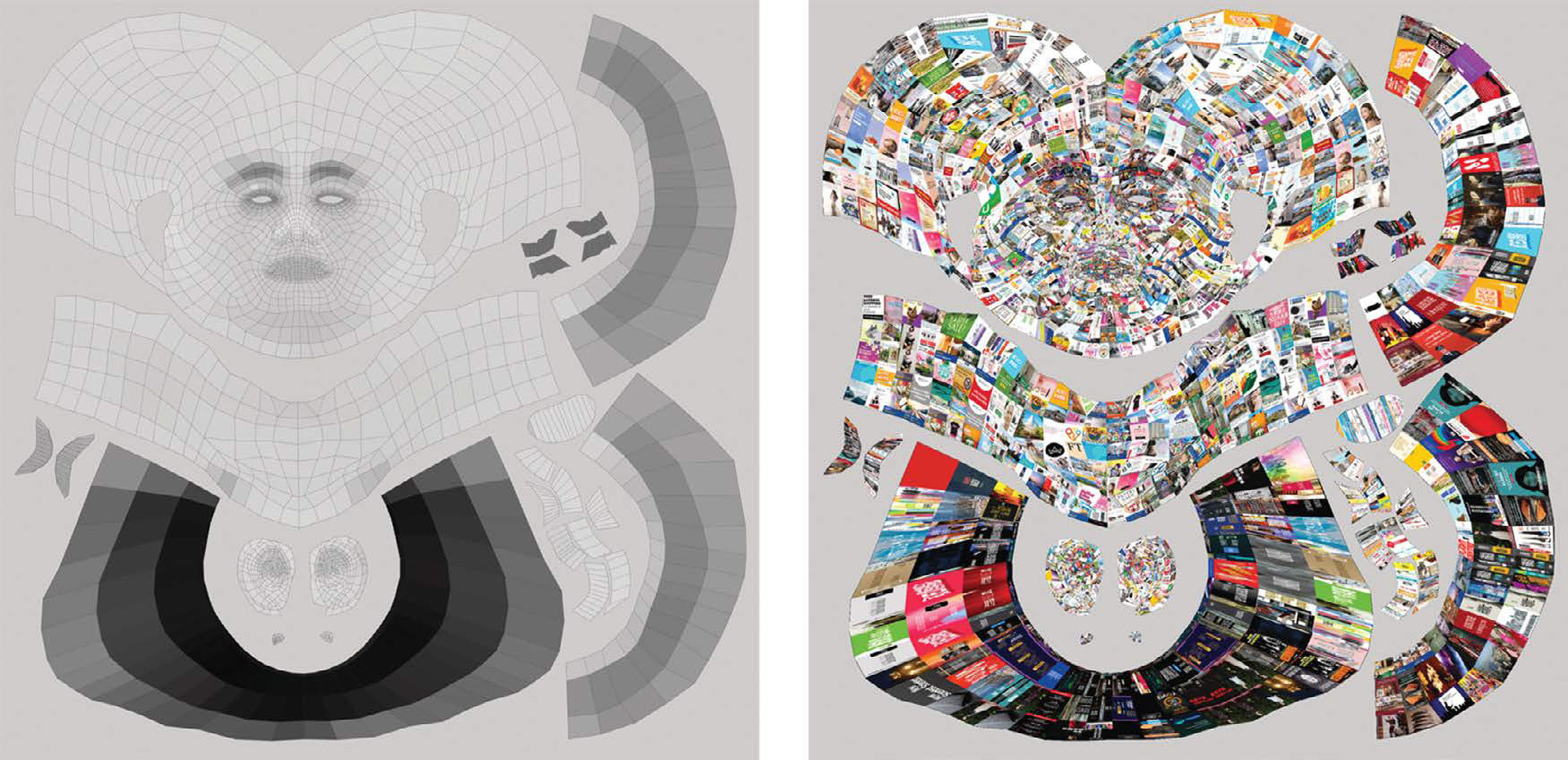
Advertising Positions integrates 3D scanning, motion capture, novel image mapping algorithms and custom animation to create data portraits from the advertisements served by online trackers. Project volunteers use bespoke software to harvest the ads they receive over months of browsing. When enough ads have been collected, the volunteer is interviewed, 3D scanned and motion captured. Each ad is then mapped to a single polygon on the textured skin of their virtual avatar. Outcomes have been displayed as 2D/3D images, animations and interactive installations.
References:
A. Soltani, A. Peterson and B. Gellman, “NSA Uses Google Cookies to Pinpoint Targets for Hacking,” The Washington Post, 10 December 2013.
1. LUMA Partners, “Display LUMAscape”: <www.lumapartners.com/lumascapes/display-ad-tech-lumascape/> (accessed January 2018).
2. L. Johnson, “U.S. Digital Advertising Will Make $83 Billion This Year, Says EMarketer”: <www.adweek.com/digital/u-s-digital-advertising-will-make-83-billion-this-year-says-emarketer> (accessed January 2018).
3. S. Yuan, J. Wang and X. Zhao, “Real-time Bidding for Online Advertising: Measurement and Analysis,” in Proceedings of the Seventh International Workshop on Data Mining for Online Advertising (New York: ACM, 2013) p. 3.
4. S. Horowitz, “What Is Real Time Bidding and Why Is It More Effective than Direct Bidding Methods?”: <http://executive-digital.com/blog/real-time-bidding-vs-direct-bidding/> (accessed January 2018).
5. M.R. Wigan and R. Clarke, “Big Data’s Big Unintended Consequences,” Computer 46, No. 6, 46–53 (2013).
6. K.D. Haggerty and R.V. Ericson, “The Surveillant Assemblage,” British Journal of Sociology 51 No. 4, 605–622 (2000).
7. D.C. Howe and H. Nissenbaum, “Engineering Privacy and Protest: A Case Study of AdNauseam,” in Proceedings of the IEEE International Workshop on Privacy Engineering (San Jose, CA, 2017).
8. D.G. McVitie and L.B. Wilson. “Stable Marriage Assignment for Unequal Sets,” BIT Numerical Mathematics 10, No. 3, 295–309 (1970).
9. J. Turow, M. Hennessy and N. Draper, “The Trade-off Fallacy: How Marketers Are Misrepresenting American Consumers and Opening Them Up to Exploitation”: <www.ftc.gov/system/files/documents/public_comments/2015/09/00012-97594.pdf> (accessed March 2018).
10. M. Schubert, Edward Burtynsky: Oil (Göttingen: Steidl, 2016).
11. J. Bryan-Wilson et al., Trevor Paglen (London and New York: Phaidon, 2018).
Additional Images: